Comprehensive Mainframe Modernization Tools & Vendors Guide 2025
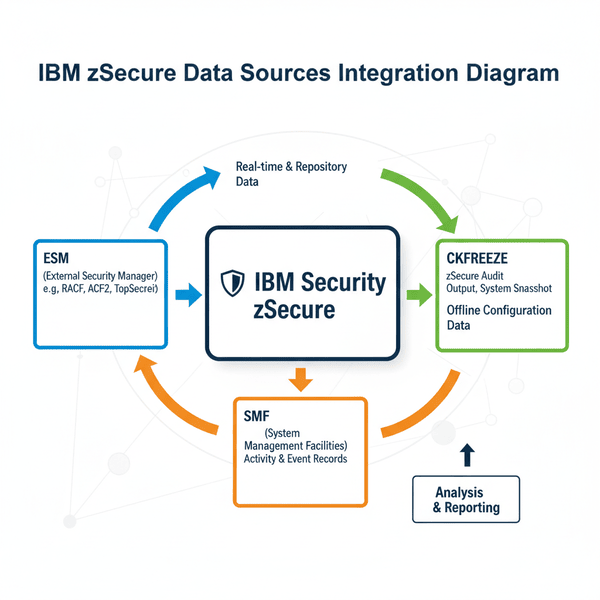
Enterprise Platform Modernization Tools 1. IBM ModernSystems & IBM Z Modernization Stack Vendor: IBMPrimary Focus: Comprehensive mainframe transformation and optimization Tools & Components: IBM Application Discovery and Delivery Intelligence (ADDI)…