Demystifying zSecure: Understanding Its Core Data Sources
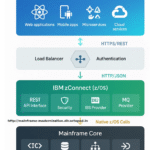
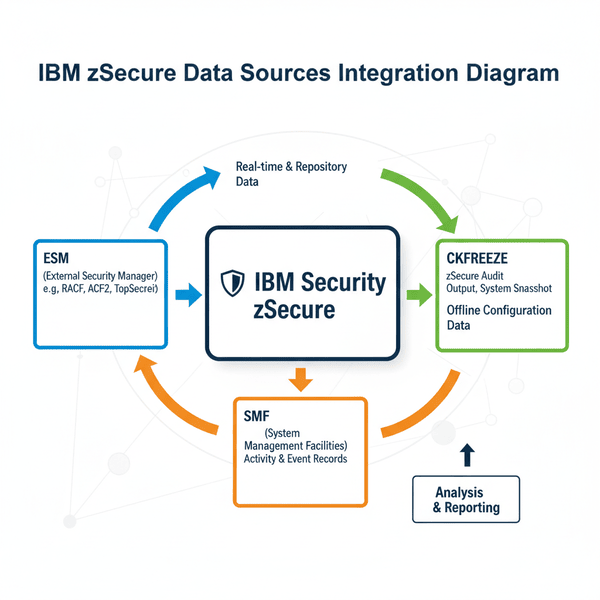
Discover how IBM Security zSecure uses ESM databases, system configuration data, and SMF logs to provide comprehensive mainframe security. Security consultant Bob Thornton explains the data sources that power effective monitoring, compliance, and threat detection in z/os RACF enterprise environments with zSecure