By Robert “Bob” Thornton, Independent Mainframe Security Consultant
After 25 years of securing mainframe environments for government agencies, healthcare organizations, and financial institutions, I’ve learned that effective security begins with understanding your data sources. Whether you’re preparing for a PCI-DSS audit, maintaining HIPAA compliance, or navigating the security complexities of a mainframe modernization project, IBM Security zSecure remains one of the most powerful tools in your arsenal—but only if you understand how it gathers and analyzes information.
In my consulting practice, I’ve seen too many organizations invest in zSecure without fully grasping the fundamental data sources that power its security intelligence. This knowledge gap creates blind spots that auditors will find, regulators will question, and threat actors may exploit. Let me walk you through the essential data sources that zSecure relies on, and more importantly, explain why each one matters from a security and compliance perspective.
The Foundation: Why Data Sources Matter for Security
Before we dive into the specific sources, let’s establish a critical principle: security without visibility is security theater. You can have the most sophisticated security policies documented in three-ring binders, but if you can’t monitor what’s actually happening on your mainframe, you’re flying blind. zSecure acts as your comprehensive security intelligence platform, but it needs the right data inputs to deliver actionable insights.
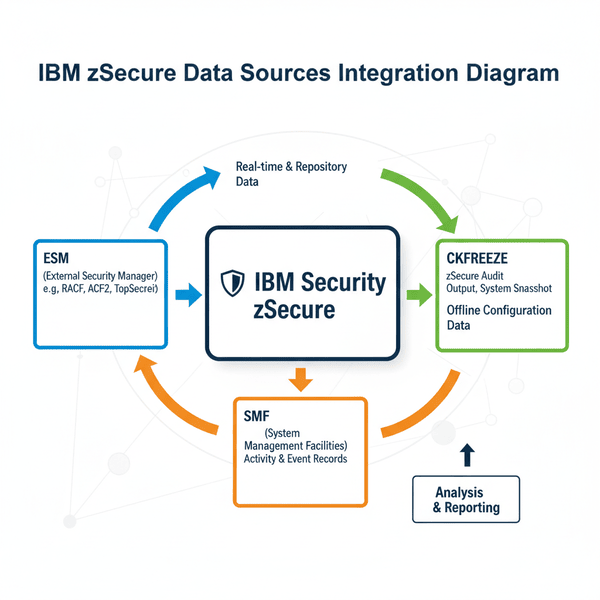
Think of zSecure as a highly trained security analyst who never sleeps. But even the best analyst needs access to the right information—the security policies, the system architecture, and the activity logs. These three pillars form the foundation of any effective mainframe security program, and they directly map to zSecure’s core data sources.
Data Source #1: The Security Database (ESM) – Your Policy Foundation
The External Security Manager (ESM)—whether you’re running RACF, CA ACF2, or Broadcom Top Secret—serves as the authoritative source for your security policy. This isn’t just a user directory; it’s the complete definition of your security posture, and in my experience, it’s where most security vulnerabilities begin.
What Lives in Your ESM
The ESM database contains three critical components that zSecure analyzes continuously:
User and Group Profiles: Every identity on your system, from the CICS service account running your transaction processing to the contractor who logged in for the first time yesterday. I’ve conducted forensic investigations where the difference between a security incident and a catastrophic breach came down to properly configured user attributes in these profiles. Pay particular attention to special attributes like OPERATIONS, SPECIAL, and AUDITOR—these are the keys to the kingdom, and zSecure helps you track every account that possesses them.
Resource Profiles: These define what’s protected and how. In a recent SOC 2 audit I supported, the auditors spent significant time examining our resource profiles for critical data sets. They wanted proof that sensitive financial data was protected with appropriate discrete profiles, not just swept under generic wildcards. zSecure’s ability to analyze your resource profile structure and identify gaps in coverage has saved me countless hours during audit prep.
Access Control Lists (Permissions): This is where theory meets reality—the actual mapping of who can do what. I once inherited a mainframe environment where 40% of the permission grants were obsolete, including UPDATE access to production payroll files for employees who’d transferred departments three years earlier. zSecure’s cross-referencing capabilities between users, groups, and resources make this kind of access certification manageable rather than overwhelming.
The Compliance Connection
From a compliance perspective, your ESM data is the evidence auditors will demand. When PCI-DSS requires quarterly access reviews, when HIPAA mandates least-privilege access controls, when SOC 2 asks you to demonstrate separation of duties—you’re pulling that evidence from your ESM data as analyzed by zSecure. I’ve testified in two litigation cases where the ESM data was the primary evidence proving (or disproving) whether adequate security controls existed at the time of an incident.
Critical Security Insight: Your ESM database represents your intended security policy. But policy and practice often diverge, which is why we need the next two data sources.
Data Source #2: System Configuration Data (CKFREEZE) – Your Environmental Context
The CKFREEZE file, generated by zSecure Collect, captures a comprehensive snapshot of your z/OS system configuration. If the ESM is your policy document, CKFREEZE is the technical blueprint of the environment where that policy must be enforced.
Why Configuration Context Matters
I learned the importance of configuration data the hard way early in my career. We had perfectly configured RACF profiles protecting APF-authorized libraries—on paper. But a configuration audit revealed that several critical system libraries weren’t actually being protected by those profiles due to a cataloging issue. Without the CKFREEZE data correlating security profiles with actual system resources, we would never have caught it.
The CKFREEZE snapshot includes:
System Parameters: IPL parameters, SVC tables, exit definitions, and TCPIP configurations. These low-level settings can create security vulnerabilities that your ESM profiles can’t address. For instance, I’ve seen systems where improperly configured SVC routines allowed privilege escalation that bypassed RACF entirely. zSecure’s analysis of CKFREEZE data can identify these configuration-based security risks.
Asset Inventory: DASD volumes, program libraries, critical datasets, and system control blocks. This inventory is essential for vulnerability assessments. When a new mainframe CVE is announced, you need to quickly determine if you’re running the affected component. CKFREEZE data makes that possible.
Security-Relevant System Resources: APF-authorized libraries, LPA modules, link pack areas, and other privileged system resources. These are prime targets for sophisticated attackers who understand mainframe internals. zSecure uses CKFREEZE data to verify that your security profiles adequately protect these high-value targets.
The Modernization Security Challenge
As organizations migrate to hybrid mainframe-cloud architectures, the security implications of system configuration become even more critical. I’m currently consulting on a project where TCP/IP port configurations and RACF SERVAUTH profiles must work in concert to secure connections between the mainframe and Azure services. The CKFREEZE data allows zSecure to verify that the configuration supports the security policy rather than undermining it.
Best Practice: Generate CKFREEZE snapshots regularly—I recommend daily for production systems. This creates a historical record invaluable for forensic investigations and change tracking. I’ve used historical CKFREEZE data to prove exactly when a security-relevant configuration change occurred during post-incident analysis.
Data Source #3: SMF Records – Your Activity Truth
System Management Facilities (SMF) records are the lifeblood of mainframe security monitoring. If ESM is your policy and CKFREEZE is your environment, then SMF is your activity feed—the constant stream of “what’s actually happening right now.”
The Power of Activity Monitoring
SMF records capture security-relevant events in real-time, including:
- Authentication attempts (SMF Type 80 records for RACF)
- Resource access attempts, both successful and denied (SMF Type 80, 83)
- Command execution, particularly privileged commands
- Security definition changes
- Dataset access patterns
- Network connection events
In my experience, SMF data separates organizations with genuine security visibility from those just checking compliance boxes. I’ve investigated numerous security incidents where SMF records provided the forensic evidence needed to reconstruct exactly what happened, when it happened, and who was responsible.
Real-World Security Scenarios
Scenario 1: Insider Threat Detection A financial services client noticed unusual after-hours data access in their zSecure alerts, generated from SMF analysis. Investigation revealed an employee downloading customer data before announcing their resignation. Without SMF monitoring through zSecure, this data exfiltration would have gone undetected.
Scenario 2: Failed Access Pattern Analysis Government agency clients are particularly interested in failed access attempts. SMF Type 80 records showing repeated access denials might indicate either an innocent user navigating permissions or reconnaissance activity by a compromised account. zSecure’s SMF analysis capabilities help distinguish between the two.
Scenario 3: Privileged Command Auditing For SOC 2 compliance, you need evidence that privileged commands are monitored and reviewed. SMF records of commands executed with elevated privileges, analyzed and reported by zSecure, provide exactly that evidence.
Integration with Enterprise Security
Modern security operations centers (SOCs) need mainframe visibility. I always recommend integrating zSecure’s SMF analysis with your SIEM platform—whether that’s IBM QRadar, Splunk, or another solution. This integration allows your security analysts to correlate mainframe events with activity across your entire enterprise, identifying attack patterns that might span multiple platforms.
Critical Consideration: SMF data is only valuable if it’s actually being collected and retained appropriately. I’ve audited environments where SMF recording was misconfigured, creating gaps in security visibility. Verify your SMF configuration regularly and ensure adequate retention for your industry’s compliance requirements.
Specialized Data Sources: The Advanced Layer
Beyond the three core sources, zSecure maintains specialized datasets that enhance its security and administrative capabilities:
Access Monitor Data: Tracks which permissions are actively used versus those that exist but remain dormant. This is gold for access certification and least-privilege initiatives. I’ve used Access Monitor data to safely remove 30-40% of excessive permissions in mature environments.
Command Logs (CKXLOG): Creates an audit trail of zSecure administrative commands. Essential for demonstrating administrative accountability and meeting separation of duties requirements.
Compliance Assertion Files: Documents accepted risks and justified exceptions to compliance rules. Critical for audit defense—it’s the difference between a finding and a documented business decision.
Bringing It All Together: A Layered Security Model
The true power of zSecure emerges when these data sources work in concert:
- ESM data tells you what the security rules should be
- CKFREEZE data shows you what the environment actually looks like
- SMF data reveals what’s really happening on the system
This three-layer validation model is essential for detecting security gaps, misconfigurations, and policy violations that would be invisible examining any single source alone.
Conclusion: Data-Driven Security Excellence
After 25 years protecting mainframe environments, I can confidently say that understanding zSecure’s data sources isn’t just technical knowledge—it’s the foundation of effective mainframe security. Whether you’re defending against external threats, detecting insider risks, preparing for audits, or securing a modernization journey, your success depends on comprehensive visibility into these three critical data dimensions.
The organizations I’ve seen suffer security incidents or fail audits typically share a common weakness: they invested in security tools without understanding the underlying data sources that power those tools. Don’t make that mistake. Master these fundamentals, configure your data collection properly, and leverage zSecure’s analytical capabilities to their fullest.
Your mainframe isn’t just a legacy system—it’s the backbone of your enterprise computing, processing your most critical transactions and protecting your most sensitive data. It deserves security practices worthy of that responsibility.
Robert “Bob” Thornton is an Independent Mainframe Security Consultant with 25 years of experience securing enterprise mainframe environments. He holds CISSP and CISM certifications and has worked with government agencies, healthcare organizations, and financial institutions on mainframe security, compliance, and modernization security challenges.